FOUR CISO SKILLS NEEDED FOR SURVIVAL
BY Maxim Frolov, Vice President of Global Sales at Kaspersky Lab
AS CYBER RISKS became a business issue, the role of the CISO in an organization has changed.
The modern CISO is not just a head of department, responsible for implementation and management of security controls - like ensuring every workstation has the latest version of endpoint security, or making sure critical ports are not exposed to the internet. It’s no longer suitable for a CISO to make their company the most secure in the world as it can hinder progress and profitability. As a C-level executive, their role is now made up of two crucial and equally important elements. Firstly, to enable the organization to achieve their business goals – such as releasing better products faster than competitors, looking attractive to stockholders, and increasing revenue.
And secondly to be a cybersecurity pro, and minimize the risks of cyberattacks that could threaten their business. Getting this balance right requires not only excellent security expertise and awareness of the latest technology trends, but a set of ‘soft’ skills, which may not come naturally to those who started their career in the IT department.
To help today’s CISOs succeed in their roles, there are four key skills to focus on.
1. Business acumen
In the good old days, the CISO was responsible for developing a defense plan based on their company’s IT landscape. This strategy is now insufficient and the modern-day approach needs to line up with the business vision. That is why almost every CISO job advertised, on Glassdoor and other sites, not only requires detailed IT security knowledge and a list of certifications, but also a business mindset.
As a result, CISOs cannot dismiss or prohibit a technology that their business would like to implement. They need to evaluate the risks associated with it and propose the most secure strategy that will not impede organizational progress. If staff need to have access to corporate resources from their devices, the CISO should implement a BYOD policy on the network.
In the words of an acting CISO, best practice involves advising others to become a risk manager as well as offering assistance and guidance to the business: “Before introducing any new technology in any department, I conduct meetings with those departments to ensure that their changes are not going against our security norms. Then we make the required changes so as to have proper integration with our network.”
2. Communication and presentation skills
Being an executive involves interacting with the C-suite and the board of directors. But with very few top managers having a security background, it can be a challenge to overcome and a CISO must develop rhetoric that ensures the board understands how serious the risks are, especially if you are used to speaking in IT jargon.
Although the ability to present complex ideas in an easy to understand manner has long been a vacancy cliché, the skill of translating cybersecurity language into business terms can fill in this communication gap. It may also help when it comes to the major headache facing every CISO – IT security budget justification. As the cybersecurity budget is often part of the overall IT expenditure, money can be prioritized for IT projects that demonstrate evident business profits and ROI. Communication skills, such as the ability to tailor information to a non-technical audience and creating strong arguments (penalties for non-compliance, damage caused by past attacks, breach reports) can prove that benefits far outweigh the costs.
3. Crisis management skills
According to a recent Kaspersky Lab report, 86% of CISOs think cybersecurity breaches will happen sooner or later, meaning that businesses cannot afford to be unprepared. Every office has an evacuation procedure that everyone must follow in case of a fire. Likewise, a company should have a strategy for when a breach happens, as panic and disorganization will only worsen the situation.
An action plan is not limited to changing affected passwords or recovering systems. To eliminate the attack quickly, it is essential to figure out who is responsible for certain actions and identify key contacts in other departments to inform first. These can include legal, PR, or customer success teams, who in turn, will be able to take part in resolving the crisis. If a breach happens, it is essential the CISO remains aware throughout an incident and becomes a link between stakeholders, who coordinates the information security team in their incident response activities, informs the business and advises further on how to resolve the situation.
4. Supervisory and leadership
With 62% of CISOs agreeing that there is a shortage in cybersecurity talent, it is becoming harder to find new security specialist. However, this is just the tip of the iceberg, and the main cause for concern is employee retention. A lack of security specialists means that workers have many job offers when they decide to change a work, as one CISO explains: “I’m a manager of very talented cybersecurity specialists, who are targets of multiple head hunters”. The lack of IT security labor force also increases the workloads of current staff, causing additional worry for security leaders. With a plethora of redundant and mundane tasks, are burnouts as inevitable as cybercrime?
As CISOs have a direct influence on security personnel, they should be a leader who people can follow, be a mentor who can support the team and find ways to motivate employees. Motivation isn’t limited to monetary incentives, it may include granting more decision-making authority, learning and professional development possibilities (for example, by attending and participating in security conferences), and even simple recognition of one’s hard work. What works perfectly for one person may not suit another, so to be an effective manager a CISO must choose the optimal incentive or source of motivation for everyone in their team.
AUTHOR'S ADDITIONAL NOTES:
It is clear that the CISO’s role is challenging, as it requires a unique combination of soft, human skills as well as hard, technical skills. To be effective, a CISO must develop management and leadership qualities, broad IT understanding, a business mindset and cybersecurity knowledge.
While technical skills form the foundation of the role today, key factors will continue to affect the balance of skills needed in the future. For example, the rise Artificial Intelligence-powered defensive tools on the market to aid the fight against cybercrime doesn’t have to mean that robots will take our jobs as they cannot learn the soft skills we’ve discussed. The day might come where machines have better cybersecurity expertise than any human and be able to solve technical tasks, but if CISOs have soft skills – like team and time management as well as business acumen – then their roles will remain a necessity for businesses in the future.
EDITOR'S NOTE:
This column is exclusively distributed by Kaspersky Media Office to selected media outlets.


Fujitsu's AI Determines Necessity of Cyberattack Responses
FUJITSU PRESS OFFICE
FUJITSU Laboratories Ltd. today announced that it has developed an AI technology that automatically determines whether action needs to be taken in response to a cyberattack.
When a business network has been hit with a cyberattack, various security appliances detect the attack on the network's servers and devices. Conventionally, an expert in cyberattack analysis then manually investigates and checks the degree of threat, to determine whether action is needed to minimize damage.
To secure the necessary training data needed to develop highly accurate AI technology, Fujitsu Laboratories has now developed a technology that identifies and extracts attack logs, which show the behavior of a cyberattack, from huge amounts of operations logs. It also developed a technology that expands on the small number of training data extracted in a manner that does not spoil attack characteristics. This generates a sufficient amount of training data.
In simulations using these technologies, they achieved a match rate of about 95% in comparison with experts' conclusions regarding the need for action, and they did not miss any attack cases that required a response. The time necessary to reach a conclusion was also shortened from several hours to several minutes.
By using these technologies, countermeasures can quickly be put in place for cyberattacks that have been determined to require action, contributing to business continuity and the prevention of loss.
Development Background
In recent years, the number of cyberattacks against business networks continues to increase. With targeted attacks(1), which is a type of cyberattack, the attacker uses clever techniques to embed malware(2) that can be controlled remotely in an organization, and then remotely controls devices infected with malware to conduct intelligence activities. In defense, when a company discovers suspicious activities with such monitoring equipment as a security appliance, a security expert manually investigates the attack, and takes time to evaluate danger and risk, then determines the necessity to respond.
The decision to respond needs to be made carefully as the responses themselves may have consequences. For example, attacked business devices may need to be isolated, and the network reconstructed, resulting in operation stoppages that impact businesses.
According to statistics from Japan's Ministry of Economy, Trade and Industry(3), by 2020 there will be a shortage of 193,000 security professionals in Japan. That being said, AI-based automation is expected to rapidly determine the necessity to respond to attack cases, making decisions on the same level as an expert who has advanced knowledge and insight on attacks.
Issues
In order to develop an AI-based model to make determinations, the following issues regarding training on attack information needed to be addressed:
1. The operations logs for normally functioning servers, devices, and network equipment coexist with the attack operations logs, and both logs are accumulated in great abundance. To conduct proper learning with AI, it is necessary to identify the traces of targeted attacks from the large number of logs. However, distinguishing between logs is difficult because intelligence activities via targeted attacks utilize OS commands and other methods.
2. It is extremely difficult to extract attack operations logs from the huge amounts of existing logs, while securing them in large quantities as training data. For AI technologies, it is possible to increase the small amounts of training data through procedures and conversions such as noise processing; however, such simple processing of the training data of targeted attacks can cause the attack characteristics to be lost, making data expansion difficult.
About the Newly Developed Technology
Fujitsu Laboratories has developed technologies to secure sufficient amounts of training data related to targeted attacks required for the creation of highly accurate, AI determination models. Features of the developed technologies are outlined below:
1. Training data extraction technology
Based on the know-how Fujitsu has accumulated in its security-related business and research, as well as from about seven years' worth of actual attack analysis data, Fujitsu Laboratories has built a database of attack patterns that includes commands and parameters linked to intelligence activities of targeted attacks. By using this database, users can accurately identify and extract a series of intelligence activities from the vast amounts of logs.
2. Training data expansion technology
This technology generates simulations of new intelligence gathering activities-a type of targeted attack-without losing attack characteristics. The technology calculates attack levels and identifies the important commands of intelligence activities in the extracted targeted attack, then converts the parameters within the range existing in the attack pattern database. As a result, it becomes possible to expand the training data fourfold.
Effects
Fujitsu Laboratories combined the newly developed technologies with its own Deep Tensor AI technology, and ran evaluative testing on the determination model that had been trained on the new training data. Run in a simulation using about four months of data-12,000 items-the technologies made an approximate 95% match with the findings that a security expert generated through manual analysis, achieving a near equal determination of response necessity.
Furthermore, the technologies were field tested on STARDUST, the Cyber-attack Enticement Platform(4) which is jointly operated with the National Institute of Information and Communications Technology (NICT), using real cyberattacks targeting companies.
The technologies automatically determined the attack cases requiring a response, thereby confirming their effectiveness.
With these AI technologies, determinations of the necessity of action, which until now have taken an expert several hours to several days, can be automatically made with high accuracy from tens of seconds to several minutes.
Furthermore, by combining these technologies with Fujitsu Laboratories' high-speed forensic technology, which rapidly analyzes the whole picture of the status of damage from a targeted attack, the response sequence, from attack analysis to instructions for action, can be automated, enabling immediate responses to cyberattacks and minimizing damage.
Future Plans
Fujitsu aims to make use of these technologies within its Managed Security Services, as a response platform for cyberattacks.
Learn More
With these AI technologies, determinations of the necessity of action, which until now have taken an expert several hours to several days, can be automatically made with high accuracy from tens of seconds to several minutes.
Symantec Introduces Advanced EDR
Tools and Fully-Managed Service to Stop the Most Dangerous Cyber Threats
Symantec Corp., the world’s leading cyber security company, today announced a new Managed Endpoint Detection and Response (MEDR) service and enhanced EDR 4.0 technology. These advancements improve attack discovery and incident response using AI-driven analytics and automation to quickly discover and stop sophisticated cyber attacks.
Enterprise IT and Security Ops teams are increasingly challenged to investigate and respond to advanced and emerging threats with available resources and staff. Symantec’s MEDR service harnesses the power of EDR 4.0 to improve incident response, threat hunting and forensics, fortifying teams with investigation expertise and threat intelligence from a world-class team of Symantec SOC analysts.
Symantec MEDR detects stealthy attacks and expertly examines suspicious activity for faster incident validation and response. A powerful combination of Symantec EDR 4.0, the SOC technology platform, and the Global Intelligence Network, allows Symantec analysts to provide 24x7 expertise. Managed threat hunting, remote investigations, and endpoint containment enable security teams around the world to stay ahead of threats. Features include:
· Industry- and region-specific analysts provide 24x7 coverage across six global SOCs.
· Managed threat hunting provides detection for zero-day and unknown threats.
· Industry best practices including MITRE ATT&CK framework help to quickly identify critical indicators of attack.
· Rapid containment of compromised endpoints using pre-authorized measures.
· Custom and emerging threat reports, business reviews, and 24x7 coverage.
“Many customers simply can’t find enough cyber security experts to meet demand. Our MEDR service provides access to Symantec’s elite SOC analysts and advanced machine learning techniques to reduce the burden on staff and shrink the time it takes to investigate incidents,” said Art Gilliland, EVP and GM Enterprise Products, Symantec. “For organizations with robust security response teams, EDR 4.0 is now available on any device, anywhere, before or after an attack occurs to provide comprehensive detection and response.”
Symantec’s EDR 4.0 continuously updates AI-driven detection engines using threat research from Symantec’s elite team of researchers and global telemetry from 175 million endpoints to train analytics to detect new attack patterns. EDR 4.0 is now available on any device, anywhere, before or after an attack. New features include:
· Advanced attack detections to help thwart “living off the land” file-less attacks.
· Automated playbooks to quickly initiate investigations.
· MITRE ATT&CK framework enrichment to expose gaps in the attack lifecycle.
· Advanced pre- and post-breach comprehensive EDR tools.
· Flexible deployment options for Symantec Endpoint Protection (SEP) and non-SEP endpoints for macOS, Linux and Windows.
“Many organizations are struggling with threat detection and incident response because of both the volume and sophistication of attacks, and an expanding attack surface. They also face many challenges including the volume of alerts and a continued reliance on manual processes,” said ESG senior principal analyst Jon Oltsik. “With a critical shortage of skilled investigators available, security teams need smart tools and services that can help them deal with the scale and speed of the modern threat environment, making it easier to identify and fix impacted endpoints. To improve IR processes, cybersecurity professionals must eschew legacy approaches and embrace the right tools and services.”
Symantec MEDR and EDR 4.0 are available now. For more information, please visit:
Learn More
New EDR innovations and industry-leading threat hunting service now available to meet the needs of organizations of all sizes

Trend Micro Warns of More Sophisticated Attacks
Trend Micro Warns More Sophisticated Cybersecurity Breaching Tactics in PH for 2019
THE dangerous but true reality of the world is that there are growing cyberthreats that are faced by consumers and organizations that are exacerbated by the increasingly connected world.
This according to a Trend Micro report, Mapping the Future: Dealing with Pervasive and Persistent Threats, highlights The report warns that attackers will increase in the effectiveness of proven attack methods, by adding more sophisticated elements to take advantage of the changing technology landscape.
“Cybercriminals will continue to follow a winning formula – exploit existing flaws, social engineering and stolen credentials – to drive profits,” said Ian Felipe, Country Manager for Trend Micro Philippines. “As both corporate attacks surface and unknown cyber threats increase, it’s more important than ever for organizations to put more resources behind cybersecurity education to help protect against these growing attacks.”
E-Celeb Accounts Will Be Abused In Watering Hole Attacks
The role of social engineering in successful attacks against businesses and individuals is predicted to increase throughout the year. It is expected that cybercriminals will compromise famous YouTubers and other “online-famous” personalities’ social media accounts, including Instagram and Twitter, by taking over their accounts via targeted phishing attacks. These will shine a light on account security in mainstream media, but not before millions of users following these accounts have been affected by whatever payload the attackers have in store for them.
Filipinos spend an average of 3 hours and 57 minutes a day on social media sites. Among their activities are following celebrities and reading their updates on Facebook, Twitter, and Instagram.
Sextortion Cases Will Rise
Sextortion, or the process forcibly demanding money or sexual favors by threatening to publish a victim’s recorded sexual activity, is a growing epidemic in the Philippines, with the country being seen as one of the crime’s biggest breeding ground. Even if there is no guarantee that a blackmailer will come through, the highly personal nature of this kind of attacks will make the victim seriously consider fulfilling the attacker’s demands, whether that means money or sexual favors. As sextortion, in particular, becomes more widespread, this kind of attacks will affect, and perhaps even claim, more lives in 2019.
Fake News Will Continue To Proliferate
The 2018 Pulse Asia Research shares that 9 out of 10 Filipinos who surf the internet to access their social media accounts are aware of fake news. Despite this awareness, the side of technology that allows fake news propagators to sway public sentiment and present itself as legitimate news has become even more powerful, which leads to governments expressing interest in regulating social media platforms. House Bill 5021 in particular, or the proposed Social Media Regulation Act of 2017, aims for social media accounts to be subjected to utmost identity verification to confirm authenticity. Trend Micro believes that this year, the improvements social media has made to fight fake news will not be enough to keep up with the deluge of cyberpropaganda. This proves to be alarming as the same survey showed that half of Filipinos who use the internet for social media have changed their views on government and politics based on what they see online.
More Cloud-Related Software Vulnerabilities Will Be Discovered
Trend Micro also predicts attackers will leverage on proven technological methods against the growing cloud adoption. According to Cloud Readiness Index 2018, the Philippines is among the countries lagging behind in cloud infrastructure and yet to mature in terms of cloud adoption. It is generally perceived that transitioning to the cloud makes users more prone to security breaches and attacks. Vulnerabilities found in cloud infrastructure, such as containers, and weak cloud security measures will allow greater exploitation of accounts for cryptocurrency mining, leading to more damaging breaches due to misconfigured systems.
Highly Targeted Attacks Will Begin Using AI-Powered Techniques
Attackers will also implement emerging technologies like artificial intelligence (AI) to better anticipate movements of top-level executives. They can use AI to determine when and where corporate executives are expected to be in the future, such as the hotels their companies typically book them in, the restaurants they pick for meetings, and other preferences that can help narrow down their next likely locations. This will lead to more convincing targeted phishing messages, which can be critical to BEC attacks. Additionally, it is likely that BEC attacks will target more employees who report to C-level executives, resulting in continued global losses.
The threat landscape promises a lot of challenges for almost all sectors of the internet-using public in 2019 even as faster internet, for better or worse, looms on the horizon. But the available tools and technologies should empower users and enterprises into positioning themselves more securely in the fight against cybercriminals and other emerging threat actors. A deep understanding of these issues is a step in the right direction.
Learn More
Trend Micro, a global leader in cybersecurity solutions, reports how Cybercriminals adapt tactics to prey upon evolving corporate technology environments. This revelation as it shared its 2019 predictions report that highlights the trends and tactics cybercriminals are most likely to employ in 2019.
To learn more about Trend Micro’s 2019 cybersecurity predictions, read the full report click the link below.

Proactively Addressing New Cyber Threat Trends in Healthcare
FORTINET PRESS OFFICE
HEALTHCARE continues to be a prime target for cybercriminals
Healthcare networks are rich with exploitable resources. Unlike retail, for example, healthcare databases not only include the financial information of their patients, but their entire personal and medical histories, often collected over years. In addition, many hospitals and medical centers serve as networking hubs for a significant number of clinics, satellite offices, and individual practices, which means that a successfully compromised network can be mined for data for a long time.
And because these networks are often so large, they are constantly in flux, making imposing consistent security extremely difficult. Providing healthcare today depends on sharing critical information – both medical and financial – across a wide variety of healthcare providers and devices. Rolling data collection and input systems, access points, and medical IoT (MIoT) are only part of the potential attack surface. As with other industries, doctors, nurses, administrators, patients, and guests all tend to blend their personal and professional lives onto a single mobile device, creating new avenues for attacking a network.
Malware detection is up 62%
This is part of the reason why exploits designed to target the data and systems of individuals and organizations are at an all-time high, with the number of unique variants showing double-digit growth. While many attacks are comprised of the minimal amount of change that allows them to avoid detection by traditional security devices, many of them are also more advanced than ever.
According to the recent Fortinet Threat Landscape Report for Q3 of 2018, the number of new malware variants based on existing exploits grew 43% last quarter. And the volume of directed attacks grew over that same time period, causing the number of unique daily malware detections per organization to rise by 62%. Because cybercriminals continue to evolve threats by creating unique malware variants and families, the ongoing importance of leveraging threat intelligence and keeping assessment tools updated has never been stronger.
Four threat trends healthcare security teams need to follow
Here are four trends we have seen over the third quarter of 2018 that healthcare security teams need to be paying special attention to:
1) Mobile devices are a growing threat vector. Exploits targeting mobile devices are a growing threat that must be addressed. Over one-quarter of organizations experienced a mobile malware attack in Q3, with the vast majority targeting the Android operating system. Compromising mobile devices allows attackers to not only steal data stored on that device, but intercept the flow of data moving between the user and the healthcare database and other connected resources. And increasingly, they can become a gateway through which the larger healthcare network can be exploited. In fact, of all the threats organizations faced last quarter from all attack vectors, 14% were Android related. By comparison, only .000311% of threats were targeted to Apple iOS.
2) Cryptojacking has become a gateway for other attacks. In many industries, cryptojacking has leapfrogged ransomware as the malware of choice. While ransomware continues to be a serious concern for healthcare networks for a variety of reasons, the number of unique cryptojacking signatures nearly doubled in the past year, while the number of platforms now being compromised by cryptojacking jumped 38%. Perpetrators include advanced attackers using customized malware, as well as “as-a-service” options available on the dark web for novice criminals. Although it is often considered to be a nuisance threat that simply hijacks unused CPU cycles, a growing number of new attack techniques include disabling security functions on devices, enabling cryptojacking to become a gateway for additional attacks. As a result, underestimating the repercussions of cryptojacking places an organization under heightened risk.
3) Botnets are getting smarter. The number of days that a botnet infection was able to persist inside an organization increased 34% during Q3, rising from 7.6 to 10.2 days, indicating that botnets are becoming more sophisticated, difficult to detect, and harder to remove. This is also the result of many organizations still failing to practice good cyber hygiene, including patching and updating vulnerable devices, protecting devices such as MIoT that can’t be directly hardened, and thoroughly scrubbing a network after an attack has been detected. The importance of consistent security hygiene remains vital to addressing the total scope of these attacks as many botnets can go dormant upon detection, only to return after normal business operations have resumed if the root cause or “patient zero” has not been rooted out.
4) Encrypted Traffic Reaches a New Threshold. Encrypted traffic now represents over 72% of all network traffic, up from 55% just one year ago. While encryption can certainly help protect data in motion as it moves between a central physical or cloud-based network and clinics, practices, and mobile healthcare professionals, it also represents a challenge for traditional security solutions. The critical firewall and IPS performance limitations of most legacy security solutions continue to limit the ability of organizations to inspect encrypted data at network speeds. And so, rather than slowing down critical medical activities, a growing percentage of this traffic is not being analyzed for malicious activity, making it an ideal mechanism for criminals to spread malware or exfiltrate data.
Addressing the Challenge
The challenge facing many healthcare organizations is that transformation efforts have spread their security resources thin, restricted visibility and fragmented the controls of many organizations. To successfully address today’s challenges, healthcare security teams need to rethink their strategy, from implementing effective security hygiene measure, to implementing an integrated security fabric architecture that can seamlessly span the entire expanding attack surface for unified visibility and the ability to orchestrate controls from a single console.
Additional strategies include:
- Countering today’s advanced threats. Digital transformation requires an equivalent security transformation. This includes a shift from point security products, manual security management, and reactive security to a strategy where different security elements are integrated into a single system, security workflows can span multiple network ecosystems, and threat-intelligence is centrally collected and correlated.
- Implementing automation. As the speed of threats rapidly increases, the time windows for prevention, detection, and remediation continue to shrink. Rapid response times are crucial, which makes the implementation of automation essential. Organizations require a security platform where each element is designed communicate with the others in real time.
- Tracking devices. One essential approach to combatting things like cryptojacking involves maintaining a comprehensive inventory of devices (especially MIoT devices) using third-generation network access controls and baselining their behavior. With this information in hand, you’re able to monitor for aberrant behavior that may reflect cryptojacking and other malicious activity.
- Addressing the threat of mobile device. More than seven in 10 clinicians in a recent survey say their hospitals support some sort of BYOD strategy. But even in hospitals and clinics where BYOD is prohibited, 65 percent of doctors and 41percent of nurses report that they still use their personal devices on the hospital network. Security leaders need to ensure they have the appropriate controls in place to protect themselves against compromised mobile devices. This requires that wireless access points and mobile security services be fully integrated into next-generation firewalls, combined with automated threat-intelligence sharing. Network access control solutions can also help establish broad device visibility combined with more granular network control.
Learn More
Most cybercriminal behavior can be reduced to two basic economic drivers. The first is to look for targets with valuable resources that can be easily turned into profits. And the second is to expend as few resources as possible to access those resources. And for both of those objectives, the networks of healthcare organizations are at the top of the list.
Sing your way to security, Kasperky suggests
unique, memorable passwords stronger than constant change, say Kaspersky Lab researchers
TO mark Change Your Password Day, 2019, Kaspersky Lab’s security researchers are advising users that unique, memorable passwords are stronger and more effective than regularly changing account passwords when it comes to keeping data secure online. The researchers have shared some easy steps that people can follow to create their own series of unique passwords. They also recommend installing a password management tool that does the hard work of remembering passwords for you.
Passwords are an established method of authentication for online accounts, but creating passwords that are both secure and memorable is not always easy, and is becoming harder as people have more online accounts. If you create simple passwords that you are unlikely to forget, the risk of an attacker cracking it are higher.
However, if you create a more complex password, you are more likely to forget it, so the chances are high that you will stick to just one or two and reuse them for multiple websites.
Kaspersky Lab researchers estimate that the greatest vulnerability of passwords is their re-use. As the recent release of more than 700 million email addresses and millions of unencrypted passwords showed, data from different breaches can easily be combined and used in ‘credential stuffing’ attacks, where hackers use victims’ email/password combinations to break into their other accounts that have the same password.
This risk is not reduced by changing passwords, but by making them strong. Further, this strength should be built not on complexity but on uniqueness.
David Jacoby, Security Researcher in Kaspersky Lab’s Global Research and Analysis Team (GReAT), said, “There is a lot of confusion about what a strong password actually means. Many websites now demand complex passwords comprising at least eight or more upper and lower case letters, numbers and special characters. This is what many users have come to equate with a ‘strong’ password, and it can seem pretty daunting.”
Jacoby adds, “The good news is that strong doesn’t have to mean scary! When you look at the issue from a security perspective, you can see that passwords are generally strong if they are unique to you and to one account. There are easy ways of making them unique, yet memorable, so that they cannot be used to breach other accounts, even if the details are exposed in a data breach. Further, there are secure password management tools available, including Kaspersky Password Manager that make it easy to safely create and use dozens of unique passwords.”
The following steps will help you to create unique, memorable passwords that are strong:
Step 1: Create your ‘static string’ (the part of the password that doesn’t change)
- Think of a phrase, song lyrics, quotes from a movie, nursery rhyme, or similar that is memorable to you.
- Take the first letter from the first three to five words.
- Between every letter add a special character: @ / # etc.
From now on, you can base all of your unique passwords on this one string.
Step 2: Add the power of association
1. When you think of the online accounts you need a password for (Facebook, Twitter, eBay, dating sites, online banking, shopping, or gaming sites etc.), write down for each the first word that you associate with that site.
2. For example, if you are creating a password for Facebook, you might associate Facebook with the blue color in the logo: so, then you can simply append the word “blue,” maybe in all caps, at the end of your static string.
David Jacoby explains, “For example, if the phrase you think of is ‘Twinkle Twinkle Little Star, How I Wonder What You Are,’ and the special character that you want to use is ‘#’, then your password for Facebook would be something like: T#T#L#S#Hblue. It makes no real sense when you look at it, or if someone gave it to you. But, since it’s personal to you, you understand the system used to generate your passwords, and you associate the word with the site, it’s easy for you to remember!”
The best way to back up, remember and securely auto-fill passwords is through a password management tool, like Kaspersky Password Manager. Kaspersky Password Manager is a secure password saver and password protection solution that allows you to create strong, unique passwords for all your online accounts, while only having to remember one master password to access them.
The most secure password manager solutions, including Kaspersky Password Manager, offer robust encryption features, so there is little threat of your data being breached by a third party.


two notorious Russian hacking groups share resources
DEADLY COLLABORATION BY sharing CYBERCRIME infrastructure
KASPERSKY Lab experts have identified an overlap in cyberattacks between two infamous threat actors, GreyEnergy – which is believed to be a successor of BlackEnergy – and the Sofacy cyberespionage group. Both actors used the same servers at the same time, with, however, a different purpose.
BlackEnergy and Sofacy hacking groups are considered to be two of the major actors in the modern cyberthreat landscape. In the past, their activities often led to devastating national level consequences. BlackEnergy inflicted one of the most notorious cyberattacks in history with their actions against Ukrainian energy facilities in 2015, which led to power outages.
Meanwhile, Sofacy group caused havoc with multiple attacks against US and European governmental organisations, along with national security and intelligence agencies. It had previously been suspected that there was a connection between the two groups, but has not been proven until now, after GreyEnergy – BlackEnergy’s successor – was found to be using malware to attack industrial and critical infrastructure targets mainly in Ukraine, and demonstrated some strong architectural similarities with BlackEnergy.
Kaspersky Lab’s ICS CERT department, responsible for industrial systems threats research and elimination, found two servers hosted in Ukraine and Sweden, which were used by both threat actors at the same time in June 2018. GreyEnergy group used servers in their phishing campaign to store a malicious file. This file was downloaded by users as they opened a text document attached to a phishing e-mail. At the same time, Sofacy used the server as a command and control centre for their own malware. As both groups used the servers for a relatively short time, such a coincidence suggests a shared infrastructure.
This was confirmed by the fact that both threat actors were observed to target one company a week after each other with spear phishing emails. What’s more, both groups used similar phishing documents under the guise of e-mails from the Ministry of Energy of the Republic of Kazakhstan.
“The compromised infrastructure found to be shared by these two threat actors potentially points to the fact that the pair not only have the Russian language in common, but that they also cooperate with each other. It also provides an idea of their joint capabilities and creates better picture of their plausible goals and potential targets," Maria Garnaeva, Security Researcher at Kaspersky Lab ICS CERT explains.
To protect businesses from attacks from such groups, Kaspersky Lab suggests customers to:
- Provide dedicated cybersecurity training for employees, educate them to always check the link address and the sender’s email before clicking anything.
- Introduce security awareness initiatives, including gamified training with skills assessments and reinforcement through the repetition of simulated phishing attacks.
- Automate operating systems, application software and security solutions updates on systems that are part of the IT, as well as enterprise’s industrial, network.
- Deploy a dedicated protection solution, empowered with behavioural-based anti-phishing technologies, as well as anti-targeted attack technologies and threat intelligence, such as the Kaspersky Threat Management and Defense solution. These are capable of spotting and catching advanced targeted attacks by analyzing network anomalies and giving cybersecurity teams full visibility over the network and response automation.
Learn More
"These findings add another important piece into public knowledge about GreyEnergy and Sofacy. The more the industry knows about their tactics, techniques and procedures, the better security experts can do their job in protecting customers from sophisticated attacks."
--Maria Garnaeva, Kaspersky Labs
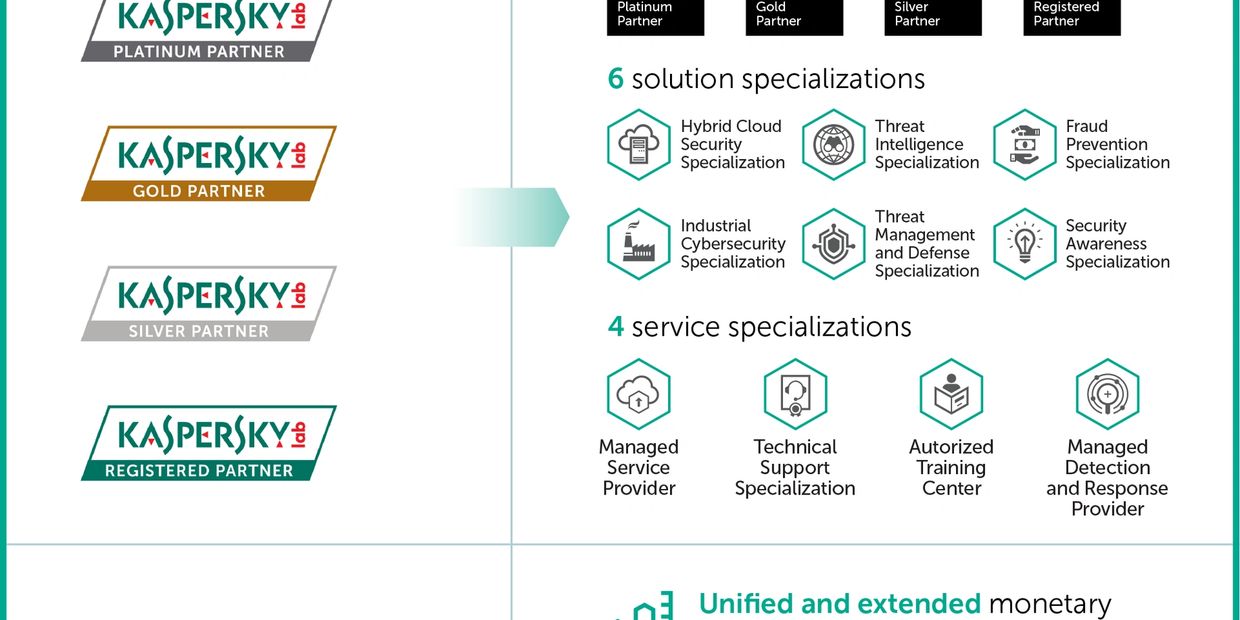
Kaspersky Lab unveils new program to empower its partners
PROGRAM IS Specialized, enabling and profitablE
Every company’s IT infrastructure is uniquely complex. As such, businesses require IT security providers with specialized cybersecurity solutions and services that address specific needs – from hybrid cloud security, to defense from targeted attacks and industrial network protection.
To help them meet these expectations, Kaspersky Lab has launched a new global partner program ‘Kaspersky United’. This program enables Kaspersky Lab partners — including resellers, service providers, and system integrators — to focus on selling the Kaspersky Lab services and products that match their own specializations. They will also receive access to education, sales and marketing toolkits and benefit from a new transparent monetary rewards scheme.
According to a Kaspersky Lab survey, when it comes to cybersecurity, the complexity of IT infrastructure is the factor that’s putting the most pressure on CISOs. Complexity widens the attack surface – it makes the protection of every aspect of infrastructure even more difficult, as it requires specific cybersecurity measures. As a result, cybersecurity providers may need to develop in-depth expertise in certain domains to offer customers specialized IT security solutions and services.
“The channel is being transformed to meet customers’ expectations, with new service offerings and business models emerging," Ivan Bulaev, Head of Global Corporate Channel, at Kaspersky Lab, comments.
Through the Kaspersky United program, partners can maintain and monetize their specializations across different status levels (Registered, Silver, Gold and Platinum) in one or several domains: by solution (hybrid cloud security, threat management and defense, or fraud prevention), or by services, such as managed service provider, managed detection and response provider, or authorized training center.
Certification in different skills or techniques can also help partners drive sales, by demonstrating to customers that they are experts in their particular areas of need.
"For example, system integrators have established security operation centers in their data centers, and offer them as a service. We are also seeing companies specialize in niche areas, delivering very specific expertise in SaaS form, such as threat intelligence platforms. We also see more and more small and medium customers moving to an IT outsourcing model and MSP business growth following this pattern," Bulaev adds.
Within the program, partners will also get comprehensive support and privileges from Kaspersky Lab, including:
· Compelling monetary rewards including significant upfront discounts, rebates on target achievement, proposal-based marketing development funds
· Specialist partner rebates of up to 20%
· Priority presales and implementation support
· Marketing and sales toolkits
· Education materials, online and offline training sessions and workshops
"To help the channel work effectively, as a vendor, we need to take these trends into account and create conditions in which each of our partners will find opportunities to develop and provide customers with the best solutions and services. That’s what we want to support through Kaspersky United," Bulaev said.
The next phase of the program will see Kaspersky Lab update the partner portal, where a variety of valuable information can be found, such as whitepapers, webinars, competitive comparisons, and certifications. New partners will gain access to specially designed Partner Onboarding training, and assets to ensure newcomers have all they need to start selling and earning more quickly.
“The new Kaspersky Partner Program is a very innovative tool for a Partner thanks to the structure of specializations, the commercial technical skills recognized as an important differentiator on the market and the constant support that the vendor guarantees. For us at Alfa Group, a Kaspersky Platinum Partner for several years, the new channel program is testimony to Kaspersky Lab’s continued investment in its partner community by recognizing even more quality, expertise and joint business opportunities.” — commented Fabrizio Mancini, Sales Director, ALFA SYSTEM S.P.A.
MORE INFO
Kaspersky United is available as of January 1, 2019. To become a Kaspersky Lab partner or achieve a specialization, please visit the portal.
PRIVACY COMMISSION OPENS QUERY ON PASSPORT DATA LEAK
Additional Information
THE National Privacy Commission (NPC) has granted the Department of Foreign Affairs (DFA) 5 more days before formally facing its preliminary fact-finding inquiry on the passport data issue.
In a meeting this morning, the NPC’s Legal and Enforcement Office asked DFA representatives headed by Director Anthony A.L. Mandap to give preliminary details surrounding the issue. Mandap said he was sent to the meeting just to “formally convey” their written request for postponement since they are “still conducting an internal investigation”. He said he could not speak beyond the scope of what was written in the request.
In the letter sent to NPC late Tuesday afternoon, the DFA’s Data Protection Officer (DPO) Menardo G. Macaraig said the DFA’s own “preliminary inquiries on the matter indicate that there was no data breach because the Asia Productivity Organization Protection Unit, a government-owned and controlled corporation and recognized government printer, remain in custody and control of said data, and that said data has not been shared with or accessed by an unauthorized third party, which may use it for illicit purposes”.
Speaking to media reporters, Privacy Commissioner Raymund Enriquez Liboro said today’s initial meeting may have been brief but productive.
“The NPC’s investigation continues. In their own preliminary probe, the DFA said it is in control of the data. That says a lot already to assuage the public. The data in question is not controlled by any unauthorized parties. That was what today’s meeting with the DFA established. The data is under their safekeeping,” Liboro said.
Commissioner Liboro looks forward to next Monday’s fact-finding meeting, which will include representatives from both the DFA and APO.
“The lessons we could learn from this incident would go a long way in ensuring better government practices. They would form part of the recommendations the NPC shall later issue to government offices contracting third parties. We’re looking to the future for ways to further protect personal data. The law obliges data controller like the DFA to strictly implement contractual means to protect data when they deal with third parties and government contractors. We look forward to improving on that based on lessons we learn here,” Liboro added.

CYBERcriminals innovate on the old ways
Lourdes C. Escolano with Raymond Gregory TRIBDINO
CYBERCRIMINALS will operate in new ways, using the same powerful technologies as the good guys but will still find the old ways of penetrating protected systems as the best entry points. This is the main prediction at the Palo Alto Networks Inc. cybersecurity forecast held recently.
Palo Alto Networks security experts Kevin O’ Leary, Field Chief Security Officer and Oscar Visaya, Country Manager for the Philippines took turns in explaining how the cybersecurity landscape will change drastically, but the channels by which breaches willl happen will remain the same.
“These predictions come from identifying really, the weakest links and finding a way to make these strong. You will notice that in the course of our discussions the intrusion points are the usual suspects. The challenge is in how stop cybercriminals as they craft their way around known protection systems—will there be the difference between an attack and and defense,” Visaya explained.
In the US over 5,000 major attacks on enterprises resulted in losses of upwards of $109B in terms of time and or data lost or stolen. The way that cybercriminals operate did not really change according to Visaya, it is how the structures of cyberprotection needs to keep up.
This should be done, according through a network security platform that is built on automation. This platform must prevent successful cyberattacks, focus on automating tasks, which means reducing human intervention as much as possible, and consume innovations fast, that means be up-to-date on what the cybercrime community is doing and developing solutions a step ahead.
For his part O’ Leary quickly discussed Palo Alto predictions for 2019.
Prediction No. 1: Business emails will come with nasty surprises. Since businesses are cybercriminals’ favorite targets, over $12B worldwide has been stolen over the past five years due to business email compromise. As the theft of passwords and login details becomes increasingly common in enterprise environments, attackers have grown more confident and motivated, targeting small and large organizations by masquerading as partners or internal stakeholders – a pattern that will continue to plague businesses if they fail to adapt.
The solution says O’ Leary is for businesses to assess their internal flow of information as well as implement more comprehensive checks and approval processes, especially with regard to the movement of resources.
“As we have seen, passwords remain amongst the weakest links in computer security – easy to steal, difficult to secure and offering little proof of a user’s identity. In response to this, 2019 will see measures such as two-factor or multi-factor authentication and biometrics become increasingly commonplace,” O’ Leary said.
Prediction No. 2: the weak link is the supply chain. Since the digital age has helped break down barriers to create an interconnected, global supply chain, making it very easy for businesses to tap suppliers and outsourced services from around the globe.
Pinpointing and avoiding cybersecurity risks will soon be nearly impossible as the global supply chain becomes increasingly complex.
“Perhaps it is time for organizations in other sectors to start asking, ‘Do we know who or which individuals, organizations and other third parties have been connecting to our networks? Do you know which systems and services your organisation is dependent on?” O’ Leary asked.
As a solution, Chief Security Officers will need to look carefully at traffic within the network to ensure sensitive information is kept separate and secure, away from external devices and systems. As multiple unsecured devices connect to corporate networks, the internet of things, or IoT, can quickly become an ‘internet of cyberthreats’.
A strong solution is to apply a Zero Trust mode to inspect and verify all traffic by placing them in a zone which only allows approved users and apps to communicate with them. In 2019, an unsecured connected device could serve as a gateway for attackers as easily as any computer or smartphone.
Prediction No. 3: Data protection legislation. As Asia-Pacific countries pledge greater cooperation with cybersecurity initiatives, the move towards formalising data protection frameworks seem inevitable. Countries like Australia and Singapore have taken the first plunge, and others in the region will soon follow as they wake up to the urgency of national security and data protection for their citizens.
In the Philippines, for example, the country has made strides for prioritizing cybersecurity with the new 2012 law: the Data Privacy Act. In addition, the Philippines recently won a seat in the International Conference of Data Protection and Privacy Commissioners (ICDPPC) after being members of the global privacy body for two years.
Prediction No. 4: Cloudy skies ahead. This app-powered era is thriving partly because of Cloud computing, which has become a go-to resource for businesses looking to deliver new products and services without bearing hefty initial investments in compute resources. Implementing a Cloud computing strategy often means that mission-critical data and systems will sit with third parties. These assets will need to be securely stored and transmitted, and only accessible to authorised personnel is of utmost importance. The security of the Cloud is not the sole responsibility of the Cloud service provider; but is shared with enterprises that also must grapple with the security of data, applications, operating systems, network configurations and more.
“To succeed, enterprises must ultimately have the processes, technology and – most importantly – people in place to keep systems adequately secured. It is critical to remember that legacy security systems, made up of various point products, have proven inadequate to prevent the rising volume and sophistication of cyberattacks. Too many security tools depend heavily on manual intervention, which can’t enact new protections quickly enough to have a meaningful impact on ongoing, targeted attacks. Reducing cyber risk requires having integrated, automated and effective controls in place to detect as well as prevent threats, known and unknown, at every stage of the attack lifecycle,” O’ Leary points out.
Prediction No. 5: why critical infrastructure is so critical. More than just a catchall term to describe public infrastructure and resources, the definition of critical infrastructure (CI) today has evolved to encompass other essential sectors, such as banking and financial services, telecommunications and the media. As CI goes digital and automated, cross-pollination between corporate and industrial networks has made them easier targets for cybercriminals. This is especially dangerous as industry systems such as supervisory control and data acquisition (SCADA) and industrial control systems (ICS), which are critical to the energy, water and public transport sectors, often rely on legacy and unpatchable systems.
Learn More
Cybercriminals innovate on how they penetrate and ransom online assets of businesses. The biggest flaw however is non-electrical, non-digital.

400% More Than Last Year: Over 8M Attacks on PH Users in Q3
FROM KASPERSKY LAB MEDIA OFFICE
Data from the Kaspersky Security Network (KSN) revealed that over three-in-10 (33.3%) users in the Philippines were attacked by Internet-borne threats from July to September. Kaspersky Lab products have detected a total of 8,133,815 malware incidents on the computers of KSN participants in the country.
This places the Philippines as the 10th most attacked country worldwide in terms of online infections for the third quarter of 2018.
"While the latest threat statistics in the Philippines are relatively lower than last quarter at 10.6 million, eight million is still alarmingly a huge leap from last year's numbers. In fact, we discovered just nearly two million online threats during the third quarter of 2017," says Yeo Siang Tiong, General Manager at Kaspersky Lab Southeast Asia.
"In the same period last year, the Philippines ranked only 35th most attacked worldwide in terms of web threats.. The young and globally known Internet savvy Filipinos are fast becoming a prime target for the money hungry cybercriminals. It’s high time that they get their defenses up."
Kaspersky Lab also discovered that online infections last quarter were detected on:
- 28.30% home users of Kaspersky Anti-virus, Kaspersky Internet Security, Kaspersky Total Security, and Kaspersky Free Anti-virus
- 9.08% business users of Kaspersky Enterprise Security
The main sources of these attacks were the United States (65.60%) followed by the Netherlands (12.31%), France (4.93%), the Philippines (3.95%), and Portugal (2.44%).
Web-based threats – or online threats – are malware programs that can target someone while using the Internet. These browser-based threats include a range of malicious software programs that are designed to infect victims’ computers.
Web threats include drive-by download that refers to the unintentional download of malicious code to one's computer or mobile device leaving it open to a cyberattack. A drive-by download can take advantage of an app, operating system, or web browser that contains security flaws due to unsuccessful updates or lack of updates.
This infection can also be done through social engineering which involves tricking the human mind to download a legitimate-looking but infected program on a computer.
Internet-borne malware have been used to steal money and confidential data as well as to serve as launch pads for bigger attacks against large companies worldwide.
“These types of attacks can be avoided with a lot of common sense and vigilance. The lack of cyber-hygiene habits plays a very significant role in cybercriminals' success. Filipinos need to be cautious with the sites they visit, files they share, apps they download, and the information they divulge online through social media platforms. Add-on a solution that holistically detects and blocks malware, and you will surely give these cybercriminals a hard time stealing your data and your money,” adds Yeo.
Similar to the global trend in web threats, most of the infections monitored against Philippine-based Internet users were malicious cryptominers.
Malicious cryptocurrency mining differs from legitimate mining only in that in the former, malefactors are using hardware that does not belong to them --- they either infect computers or lure victims on mining websites.
The top five most attacked countries during Q3 2018 include Algeria (45%), Venezuela (40.7%), Belarus (40.5%), Albania (39.0%), and Moldova (37.9%).
About Kaspersky Security Network
Kaspersky Security Network (KSN) is a complex distributed infrastructure dedicated to processing cybersecurity-related data streams from millions of voluntary participants around the world. The statistics in this report are based on completely anonymous data obtained from Kaspersky Lab products installed on users' computers in the Philippines. This technology assists Kaspersky Lab in the swift detection of new malware, identification of its source, and blocking of its launch on users' computers. It generates reports for countries with more than 10,000 Kaspersky users.
About Kaspersky Lab
Kaspersky Lab is a global cybersecurity company, which has been operating in the market for over 20 years. Kaspersky Lab’s deep threat intelligence and security expertise is constantly transforming into next generation security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky Lab technologies and we help 270,000 corporate clients protect what matters most to them.
Integrated ops center is bank’s watchtower
Gregory E. Bautista
TO enable better customer experience, secure it from attacks, ensure all branch operations are always connected and translate its presence into maximized revenues, Unionbank of the Philippines revealed its Integrated Operations Center (IOC) to a few lucky journalists who have entered its double doors, quadruple security accesses with biometrics and passcode.
But the coverage “never” happened. And the select members of the media “were not” led to a high-tech central command watchtower that looked more like a Mars-landing operations than a bank.
“It was designed to be operate like a Formula 1 team where critical data is used to make quick decisions. In our case, the IOC will supply the bank the business telemetry needed to make the right decisions to ensure we are at peak performance in terms of revenue and in keeping our customers happy,” Dennis Omila, UnionBank Executive Vice President and Chief Information Officer explained.
It is a first-of-its-kind collaborative facility in the country. Highlighting the use of Artificial Intelligence (AI) and deep Machine Learning (ML) to do predictive analysis on various bank activities it operates under its Business Intelligence Center. Smooth integration is then done with the Security Operations Center where a huge LED screen monitors real time malware detections and scans from several cybersecurity vendors.
There are screens all over the IOC monitoring critical items that have to do with daily financial transactions, branch business operations as well as customer activation and engagement.
What is really impressive is how automated the operations are.
“The people who man the center provide the human touch to it,” explained Charmaine Valmonte, Head of IT Risk Management and Resiliency, UnionBank said as she said that left alone, the center can operate on its own and warn the personnel of specific “flags” or actions that may require human intervention.
In the Security Center for example, the various cybersecurity platforms running simultaneously were already busy reading possible emails that may contain phising threats and isolating these for quarantine, while others were indicating points in the map where possible fintech attacks were happening.
The IOC is more than a watchtower. Valmonte said the IOC stands as the “fabric” of UnionBank’s digital transformation initiative where the intertwined operations of financial management, security, customer service and branch management happen. It allows the team to be proactive and predictive to a certain extent.
“With a well-coordinated and well-trained team, the business drivers will spend less time in the pit stop,” Omila said referring back to their F1 race metaphor.
“It’s part of the fabric of our transformation. We need to keep an eye on everything - the system and processes as well as how our clients feel,” Valmonte told reporters.
UnionBank saw a 57 percent-drop in its severity incidents to three in 2017 from seven a year ago. Apart from this, the bank also saw in 2017 increased uptime for branches and offsite ATMs to 99.23 percent and 96.38 percent respectively, from 2016.

Fake Facebook sites are 60% Of social network phishing
Kaspersky Lab’s anti-phishing technologies prevented more than 3.6 million malware attempts
24 May 2018
In the first quarter of 2018, Kaspersky Lab’s anti-phishing technologies prevented more than 3.6 million attempts to visit fraudulent social network pages, of which 60% were fake Facebook pages. The results, according to Kaspersky Lab’s report, ‘Spam and phishing in Q1 2018’, demonstrate that cybercriminals are still doing what they can to get their hands on personal data.
Social network phishing is a form of cybercrime that involves the theft of personal data from a victim’s social network account. The fraudster creates a copy of a social networking website (such as a fake Facebook page) and tries to lure unsuspecting victims to it, forcing them to give up their personal data – such as their name, password, credit card number, PIN code, and more – in the process.
At the beginning of the year, Facebook was the most popular social networking brand for fraudsters to abuse, and Facebook pages were frequently faked by cybercriminals to try and steal personal data via phishing attacks.
This is part of a long-term trend: in Q1 2017, Facebook became one of the top three targets for phishing overall, at nearly 8%, followed by Microsoft Corporation (6%) and PayPal (5%).
In Q1 2018, Facebook also led the social network phishing category, followed by VK – a Russian online social networking service - and LinkedIn. The reason for this is likely to be the worldwide 2.13 billion active monthly Facebook users, including those who log in to unknown apps using their Facebook credentials, thereby granting access to their accounts. This makes unwary Facebook users a profitable target for cybercriminal phishing attacks.
The distribution of different types of social network phishing detected by Kaspersky Lab in Q1 2018
This all reinforces the fact that personal data is valuable in the world of information technology both for legitimate organizations and attackers. Cybercriminals are constantly searching for new methods to hit users, so it’s important to be aware of fraudster techniques to avoid becoming the next target.
For example, the latest trend is spam emails related to GDPR (Europe’s General Data Protection Regulation). Examples include offers of paid webinars to clarify the new legislation, or invitations to install special software that will provide access to online resources to ensure compliance with the new rules.
“The continuous increase in phishing attacks --- targeting both social networks and financial organizations --- shows us that users need to pay more serious attention to their online activities. Despite the recent global scandals, people continue to click on unsafe links and allow unknown apps access to their personal data. Due to this lack of user vigilance, the data on a huge number of accounts gets lost or extorted from users. This can then lead to destructive attacks and a constant flow of money for the cybercriminals,” said Nadezhda Demidova, lead web content analyst at Kaspersky Lab.
Kaspersky Lab experts advise users to take the following measures to protect themselves from phishing:
- Always check the link address and the sender’s email before clicking anything. Even better, don’t click the link, but type it into your browser’s address line instead.
- Before clicking any link, check if the link address shown, is the same as the actual hyperlink (the real address the link will take you to). This can be checked by hovering your mouse over the link.
- Only use a secure connection, especially when you visit sensitive websites. As a minimum precaution, do not use unknown or public Wi-Fi without a password protection. For maximum protection, use VPN solutions that encrypt your traffic. And remember: if you are using an insecure connection, cybercriminals can invisibly redirect you to phishing pages.
- Check the HTTPS connection and domain name when you open a webpage. This is especially important when you are using websites which contain sensitive data – such as sites for online banking, online shops, email, social media sites etc.
- Never share your sensitive data, such as logins and passwords, bank card data etc., with a third party. Official companies will never ask for data like this via email.
- Use a reliable security solution with behavior-based anti-phishing technologies, such as Kaspersky Total Security, to detect and block spam and phishing attacks.
Other key findings in the report include:
Phishing:
- The main targets of phishing attacks have remained the same since the end of last year. They are primarily global Internet portals and the financial sector, including banks, payment services and online stores.
- About $35,000 USD was stolen through one phishing site that appeared to offer the opportunity to invest in the rumored Telegram ICO. Approximately $84,000 USD was stolen following a single phishing email mailshot related to the launch of ‘The Bee Token’ ICO.
- Financial phishing continues to account for almost half of all phishing attacks (43.9%), which is 4.4% more compared to the end of last year. Attacks against banks, e-shops, and payment systems remain the top three, demonstrating cybercriminals’ desire to access users’ money.
- Brazil was the country with the largest share of users attacked by phishers in the first quarter of 2018 (19%). It was followed by Argentina (13%), Venezuela (13%), Albania (13%), and Bolivia (12%).
Spam:
- In the first quarter of 2018, the amount of spam peaked in January (55%). The average share of spam in the world’s email traffic was 52%, which is 4.6% lower than the average figure of the last quarter of 2017.
- Vietnam became the most popular source of spam, overtaking the U.S. and China. Others in the top 10 included India, Germany, France, Brazil, Russia, Spain, and the Islamic Republic of Iran.
- The country most targeted by malicious mailshots was Germany. Russia came second, followed by United Kingdom, Italy, and the UAE.
Learn More
To learn more about spam and phishing in Q1 2018, read our blogpost on Securelist.com. Click the action button below.
DDoS attacks may have hit you
You may have been hit but not know it
Over a quarter of businesses that have been hit by a Distributed Denial of Service (DDoS) attack don’t think they were the intended target, highlighting that businesses can’t afford to be complacent when it comes to today’s threat landscape. According to research* from Kaspersky Lab, 27% of respondents said being an innocent bystander was the most likely reason for DDoS attacks on their organization, suggesting that all businesses are in the firing line, even when they are not on the hit list.
The continued threat of DDoS attacks and the value that they bring to those that deploy them – from halting company operations, through to accessing confidential information or demanding a ransom – means that all businesses are potential targets. Despite this, organizations are still showing signs of cyber-complacency, with 28% not using specialized anti-DDoS protection because they believe they are unlikely to be targeted by DDoS attacks.
However, this complacency is misplaced. Of the companies that experienced a security incident within the last 12 months, 44% blamed a DDoS attack as being a contributing factor to that incident – up from a quarter (25%) in 2016. This shows the impact of these types of attacks in today’s workplace and the need for organisations to proactively defend themselves against them.
It’s not just unintended attacks that firms must be ready to ward off at a moment’s notice. Nearly a quarter (23%) of businesses believe a competitor was behind a DDoS attack on their organisation – most likely for espionage or disruption purposes; 24% believed it was used as a distraction tactic to hide another attack from IT staff, and 24% believe that a DDoS attack was designed to specifically disrupt their operations.
“A worryingly large proportion of businesses are still displaying an ‘it won’t happen to me mentality’ towards DDoS attacks, which they simply can’t afford to do in today’s threat landscape,” commented Alexey Kiselev, Project Manager on the Kaspersky DDoS Protection team. “The number of attacks, combined with the range of targets that have been discovered over the last 12 months, has shown that no business is safe from cybercriminals and, as such, organisations must be prepared to take responsibility for their cybersecurity. When it comes to protecting critical data and keeping operations up and running, there is simply no room for complacency.”
With the financial consequences of DDoS attacks ranging from fighting against the attack itself, to a loss of revenue or business opportunities, it’s certainly better to be safe than sorry. That’s where Kaspersky DDoS Protection comes into play, providing a fully-integrated solution with advanced intelligence capabilities to protect businesses of all sizes from the most complex and high-volume DDoS attacks. More information can be found here.
*The IT Security Risks research is an annual survey conducted by Kaspersky Lab in conjunction with B2B International. In 2017 we asked 5,274 representatives of small, medium (50 to 999) and large businesses (1000+) from 29 countries about their views on IT security and the real incidents that they have had to deal with.

Cookie Policy
Techsauceph.com uses cookies for purposes of tracking and usage only. No personal information is collected. Techsauceph complies with the Philippine Data Privacy Act of 2012